Are austinbased network access control elsewhere you tired of constantly worrying about network security threats? Are you looking for a solution to protect your business from unauthorized access, malware attacks, and data breaches? Look no further than Austin-based Network Access Control (NAC) solutions! In this blog post, we’ll dive into the world of NAC and explore why it’s becoming an essential tool in securing corporate networks. Whether you’re a small-business owner or an IT professional seeking ways to keep your company’s digital assets safe, read on to learn more about how NAC can help!
What is Austin-based network access control?
Austin-based network access control (NAC) provider SentryOne is one of the few providers in the country with a full suite of NAC features and capabilities. This comprehensive suite provides administrators with comprehensive tools to manage and protect their networks from unauthorized users.
SentryOne offers three different types of NAC services:
The company’s centralized management console gives administrators complete control over their entire network, including all devices that connect to it. Administrators can monitor activity on all devices, enforce policies and rules, and remotely manage users and devices.
What are the benefits of using Austin-based network access control?
Austin-based network access control (NAC) solutions provide organizations with a variety of benefits, including increased security and compliance, reduced administra tive costs, and better user experience.
Network access control helps protect your organization’s assets by enforcing policies that restrict who can access your network. By enforcing these policies, you can ensure that only authorized individuals have access to your resources, which increases security and compliance. In addition, NAC solutions can help reduce administrative costs by automating some of the tasks associated with authorizing users. Finally, NAC technologies can improve user experience by providing a streamlined interface that makes it easier for administrators to manage users and settings.
How does Austin-based network access control work?
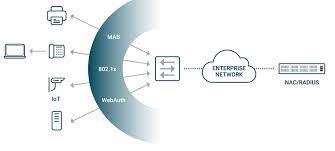
Austin-based network access control (NAC) works by using a variety of technologies, including firewalls, intrusion detection/prevention systems (IDS/IPS), and traffic management systems, to identify and block unauthorized users from accessing company resources. By using these tools together, NAC can help prevent data breaches, protect intellectual property, and minimize the potential for security threats.
NAC can be deployed in a variety of ways, depending on the needs of the organization. Some organizations may opt for a centralized approach where all users are monitored and tracked centrally. Other organizations may choose to implement NAC in a distributed fashion, where employees’ devices are monitored but not blocked outright. Regardless of the configuration, NAC should be regularly updated to keep up with evolving threats.
What types of security measures can Austin-based network access control provide?
Austin-based network access control (NAC) solutions can provide a variety of security measures to help protect your company’s networks and data.
NAC solutions can monitor traffic and users, enforce policies, and protect against unauthorized access. They can also detect and prevent malicious software from attacking your systems.
Some common NAC features include:
• Software authentication: Enforce authentication requirements for network access to prevent unauthorized access.
• firewalls: Block unwanted traffic by blocking ports, IP addresses, or protocols.
• intrusion detection systems (IDS): Detect signs of an attack before it occurs and take steps to stop it.
• user profiling: Profile users and assign them specific austinbased network access control elsewhere levels of access privileges based on their role in the organization.
Conclusion
network access control (NAC) is an essential security technology for businesses of all sizes. In this article, we’ll highlight some of the best Austin-based NAC providers to help you make the right choice for your needs. By reading this article and researching on your own, you’ll be better equipped to choose the provider that’s right austinbased network access control elsewhere for your company and its specific security needs. Thanks for taking the time to read!